Solutions for Establishing a Secure Automotive Software Development Process

Trends, and cybersecurity standards and regulations
The automotive industry is seeing several major trends driving advancements for the next-generation vehicles. These trends are commonly referred to as CASE: connected, autonomous, shared and services, and electrification. It is important to recognize that for the automotive industry to allow the development and deployment of connected and autonomous vehicles, including electric vehicles, which provide greater user experience by enabling access to various mobility-sharing and additional services, cybersecurity is paramount. These future vehicles need to be cybersecurity-protected against malicious attackers who may target remote interfaces and vulnerabilities in automotive systems. Moreover, to achieve these advancements, there is a fundamental shift from mechanical and electrical solutions to software-based solutions providing the required vehicle functionality. Thus, future vehicles will contain more advanced and complex systems based on large software codebases. More software typically inherently has higher risk of more vulnerabilities and therefore automotive organizations need to emphasize the establishment of a secure software development process.
Furthermore, cybersecurity has been gaining a stronger focus in past years with the development and introduction of various standards and regulations. A draft standard of the ISO/SAE DIS 21434 “Road vehicle – cybersecurity engineering” [1] was released in February this year. The standard has received several comments and is currently being updated and the final version is expected to be released in the first half of 2021. This standard presents various requirements and recommendations for automotive organizations on several topics including overall cybersecurity management, project-dependent cybersecurity management, continuous cybersecurity activities, risk assessment methods, concept, product development, and post-development phases. Additionally, in June this year, two new UN regulations on Cybersecurity and Software Updates were adopted by UNECE’s World Forum for Harmonization of Vehicle Regulations (WP.29) [2]. These regulations focus on a framework and processes for automotive organizations to be able to among other identify and manage security risks in vehicle design, ensure risk assessments are kept current, monitor and respond to cyber-attacks, and assess if cybersecurity measures remain effective in light of new threats and vulnerabilities. The two UN regulations emphasize mainly on the need for organizations to establish a CSMS (cybersecurity management system) and SUMS (software update management system).
It is also worth noting that the OpenChain Working group has been working on a new ISO standard focusing on requirements for an open-source license compliance program to allow for building trust between organizations exchanging software solutions comprised of open-source software[3]. As mentioned above, with larger software codebases, including increased usage of open-source software (OSS) components in automotive systems, it becomes imperative to manage OSS in the automotive supply chain. Although the OpenChain ISO standard focuses on license compliance, it is equally important to achieve software component transparency in the supply chain. Software component transparency is actively promoted by the National Telecommunications and Information Administration (NTIA) of the United States Department of Commerce [4]. Activities promoted by NTIA include defining and using SBOM (software bill-of-materials), how to identify and name components, how to share SBOMs between parties, and how to automate SBOM production. The main purpose of these activities is to enable a process to allow involved parties in the supply chain to be aware of especially included OSS components and associated known vulnerabilities to be able to address any potential security concerns.
With an understanding of these trends, standards and regulations, this article further explores common challenges that lead to vulnerabilities in automotive systems and highlights automated solutions to help automotive organizations establish a secure software development process.
Cybersecurity challenges in the automotive software development lifecycle
A report based on a survey called “Securing the Modern Vehicle: A Study of Automotive Industry Cybersecurity Practices” was released in February 2019. This report was commissioned by SAE International and Synopsys, and the survey was conducted independently by the Ponemon institute [5]. The report contains results based on a survey of security experts in the automotive industry involved in the development of automotive systems. One example from this report is highlighted in Figure 1. The figure shows the answer to the question: “What are the primary factors that lead to vulnerabilities in automotive software/technology/components?”
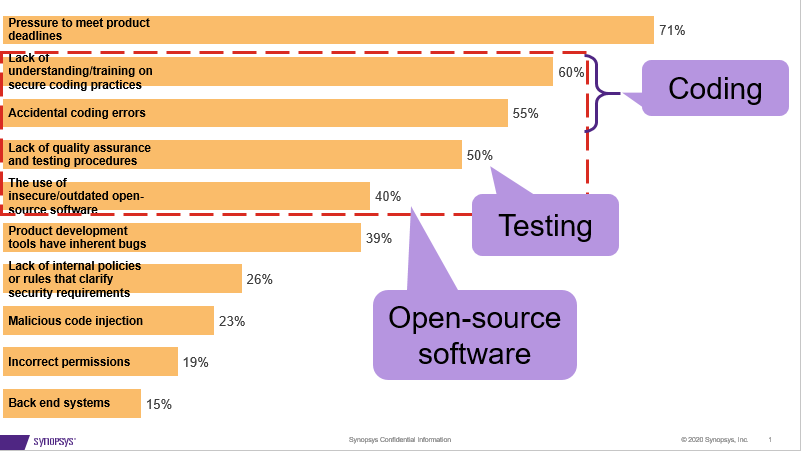
Besides the top factor “Pressure to meet product deadlines”, the top three factors are related to coding, testing, and open-source software. Regarding coding, factors include “Lack of understanding/training on secure coding practices” and “Accidental coding errors”. Regarding testing, the factor is related to “Lack of quality assurance and testing procedures”. Finally, regarding OSS, the related factor is “The use of insecure/outdated open source software components”. Thus, it is clear that while there are substantial benefits with more vehicle functionality controlled by software, it also introduces more risks for software vulnerabilities in the application layer due to coding errors, lack of testing, and the use of vulnerable OSS components.
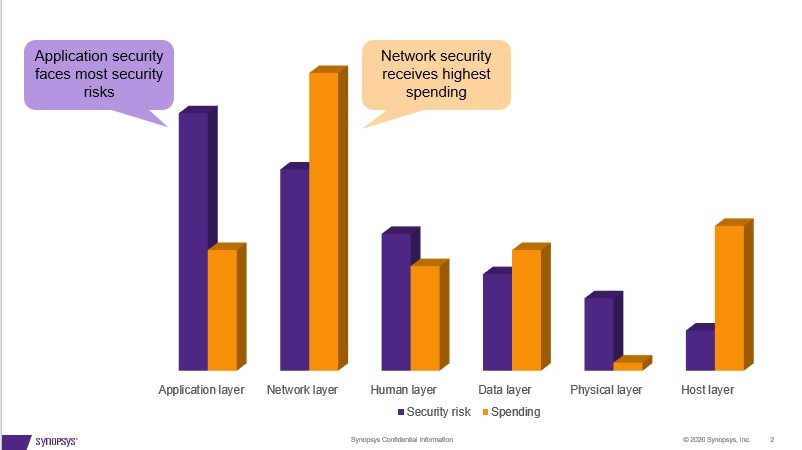
These results from the automotive survey show similarities to the IT and enterprise industries where according to SAP, 84% of cyber attacks happen on the application layer, which makes it the most targeted attack surface for attackers [6]. However, as shown in Figure 2, security spending is disproportionate: while application security faces the most security risks, network security receives the highest spending. This information could serve as a guide for the automotive industry that there needs to be an increased focus on application security testing solutions.
Solutions to establish a secure software development process
It is worth noting that while ISO/SAE DIS 21434 and UNECE WP.29 provide a more holistic view of cybersecurity including describing multiple cybersecurity activities on both organizational and project levels, this article focuses especially on cybersecurity solutions for the software development lifecycle. More specifically, the focus is on applicable solutions to address the top three factors from the above-mentioned automotive survey report namely: coding, testing, and OSS. In the following, corresponding application security testing solutions that automotive organizations can deploy during the software development lifecycle to help identify and fix vulnerabilities earlier are presented. Since automotive organizations often have limited security resources, the focus is on automated solutions rather than manual activities. Figure 3 gives an overview of how these application security testing solutions are mapped to the three challenges.
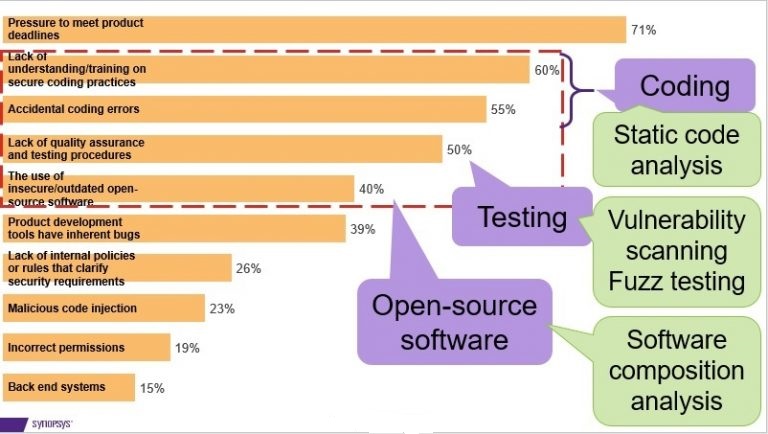
Regarding coding, requirement [RQ-10-12] in ISO/SAE DIS 21434 [1] states that verification activities shall be performed and that static code analysis can be used as a verification activity for software to search the source code for patterns matching known faults, common weaknesses and vulnerabilities. Static code analysis tools, e.g., Coverity [9], allow for analyzing the source code without executing the software which also means that manual activities to define any test cases can be avoided. These tools can help find buffer overflows, resource leaks, memory corruption and other issues in the software code. Moreover, requirements [RQ-10-20] and [RQ-10-21] in ISO/SAE DIS 21434 [1] state that coding guidelines shall be used when cybersecurity is not sufficiently addressed by the programming language itself, and that the software shall be verified for compliance with the coding guidelines. Static code analysis tools can be used by automotive organizations to verify compliance to such coding guidelines, e.g., MISRA C/C++, AUTOSAR C++, and CERT C/C++. Moreover, it is important to recognize that a static code analysis tool by itself is not as useful as having the tool work in an automated fashion for the relevant projects as part of the CI (continuous integration) pipeline in the software development process. Thus, automotive organizations need to consider approaches for rolling out tool usage to large relevant development teams, including ensuring scalability and performance. Additionally, it may be necessary to prepare enablement material for developers, including specific “how to” guides for safety or security-related projects, including compliance with certain coding guidelines. Last, to ensure efficiency and effectiveness of the tools, it is necessary for automotive organizations to consider how to integrate the static analysis tools with other tools in the software development lifecycle to achieve automation, including source code management systems, automation servers, build systems, and bug tracking systems.
Regarding testing, recommendation [RC-10-03] in ISO/SAE DIS 21434 [1] states that component testing should be performed to search for unidentified vulnerabilities. In addition, requirement [RQ-10-18] in ISO/SAE DIS 21434 [1] states that weaknesses and vulnerabilities identified in [RC-10-03] shall be managed by the automotive organization in a defined vulnerability management process. There are numerous test approaches that can be applied to search for unidentified vulnerabilities including vulnerability scanning, fuzz testing, and penetration testing. Vulnerability scanning uses knowledge of known vulnerabilities or attack patterns to identify vulnerabilities on the target system. While vulnerability scanning tools typically use a database of known vulnerabilities or attack patterns, fuzz testing as a technique goes further to identifying unknown vulnerabilities by generating malformed input that is then provided to the target system. Fuzz testing tools, e.g., Defensics [10], can be used to identify unknown vulnerabilities in various protocol implementations on automotive systems including CAN, CAN-FD, Automotive Ethernet, Wi-Fi, Bluetooth etc. as well as upper layer protocols such as ISO-TP, UDS, DoIP, gPTP, IP, TCP, HFP, A2DP etc. While vulnerability scanning and fuzz testing can generally be performed using automated tools during the software development process, penetration testing typically involves manual activities performed in several steps including planning, discovery, attack, and reporting. During a penetration test, although some automated tools can be used, a human tester mimics a “real” attacker to try to break certain security goals of the target system [11]. Moreover, it is important to note that automotive organizations should consider approaches for applying automated test tools such as vulnerability scanning and fuzz testing tools in an automated fashion as part of the CI pipeline in the software development process. This includes determining which tools to use, when and what to test, what test environments are required and how often testing should occur. Furthermore, it is necessary to consider how to integrate with other tools in the software development lifecycle, such as automotive test tools and automation servers. It is also important for automotive organizations to consider establishing dedicated cybersecurity test labs to enable automated security testing.
Regarding OSS, requirement [RQ-06-16] in ISO/SAE DIS 21434 [1] states that when integrating an off-the-shelf component, e.g., an OSS component, cybersecurity-relevant information such as known vulnerabilities shall be gathered and analyzed. One overarching goal for automotive organizations is to achieve software transparency in the automotive software supply chain. Software composition analysis can be used to help achieve this goal. Software composition analysis tools, e.g., Black Duck [12] can scan the target software in the form of source code or binary to identify included OSS components and corresponding versions. This information is useful to help automotive organizations to avoid the usage of outdated OSS components. Additionally, these tools can be used to automatically generate SBOMs in an agreed format, e.g., SPDX (Software Package Data Exchange) that can be shared together with the software along the supply chain. More importantly, from a security perspective, software composition analysis tools can also map known vulnerabilities to the identified OSS components using vulnerability databases such as NVD (national vulnerability database). Furthermore, requirement [RQ-07-01] in ISO/SAE DIS 21434 [1] states that internal and external sources shall be monitored for collection of cybersecurity information. As an external source, software composition analysis tools can provide alerts and additional information on newly identified vulnerabilities in OSS components as input to the continuous cybersecurity monitoring activity at automotive organizations. Finally, not specifically related to security, but equally important from a license compliance point of view is that these tools can also identify the relevant associated license types to help automotive organizations ensure that they are compliant with the license terms. Moreover, it is imperative that automotive organizations consider approaches to ensure that the software composition analysis tool is applied in an automated fashion for relevant projects as part of the software development process. For example, this includes establishing an overall process for OSS management that defines when and what to scan, applying OSS policies including criteria for acceptable OSS usage, and defining an approval process for using new OSS components. In addition, automotive organizations should consider how to integrate software composition tools with other tools in the software development lifecycle, such as source code management systems, automation servers, build systems, and bug tracking systems.
Summary
With the continued advancements of CASE, introduction of new cybersecurity standards and regulations, cybersecurity is becoming a major focus area for the automotive industry. Especially regarding automotive software development, the three main challenges are related to coding, testing and OSS. To address these challenges automotive organizations can deploy automated application security testing solutions such as static code analysis tools, vulnerability scanning tools, fuzz testing tools, and software composition analysis tools. As mentioned, while it is important to use appropriate application security testing tools in the software development lifecycle, it is equally important for automotive organizations to establish the necessary processes to enable effective use of the tools. Especially, this requires considerations for integration with other tools and systems, defining processes for when and what to test, and finally running the tools in an automated fashion in a CI pipeline.
References
[1] ISO/SAE, “ISO/SAE DIS 21434 Road vehicles — Cybersecurity engineering”, https://www.iso.org/standard/70918.html
[2] UNECE, “UN Regulations on Cybersecurity and Software Updates to pave the way for mass roll out of connected vehicles”, https://www.unece.org/info/media/presscurrent-press-h/transport/2020/un-regulations-on-cybersecurity-and-software-updates-to-pave-the-way-for-mass-roll-out-of-connected-vehicles/doc.html
[3] ISO/IEC, “ISO/IEC DIS 5230 Information technology — OpenChain Specification”, https://www.iso.org/standard/81039.html
[4] NTIA, “NTIA Software Component Transparency”, https://www.ntia.doc.gov/SoftwareTransparency
[5] Ponemon Institute, “Securing the Modern Vehicle: A Study of Automotive Industry Cybersecurity Practices”, 2019, https://www.synopsys.com/auto-security
[6] Forbes, ” Most Cyber Attacks Occur From This Common Vulnerability”, https://www.forbes.com/sites/sap/2015/03/10/most-cyber-attacks-occur-from-this-common-vulnerability/#1ef450857454
[7] Digital Guardian, “Infographic: Is Security Spending Proportional to the Data Breach Problem?”, https://digitalguardian.com/blog/infographic-security-spending-proportional-data-breach-problem
[8] Ponemon Institute, “How to Make Application Security a Strategically Managed Discipline”, 2016
[9] Synopsys, “Coverity Static Application Security Testing”, https://www.synopsys.com/software-integrity/security-testing/static-analysis-sast.html
[10] Synopsys, “ Defensics Fuzz Testing”, https://www.synopsys.com/software-integrity/security-testing/fuzz-testing.html
[11] Stephanie Bayer, Thomas Enderle, Dennis Kengo Oka, Marko Wolf, “Security Crash Test – Practical Security Evaluations of Automotive Onboard IT Component”, Automotive Safety & Security, 2015
[12] Synopsys, “ Black Duck Software Composition Analysis”, https://www.synopsys.com/software-integrity/security-testing/software-composition-analysis.html
Author:
Dr. Dennis Kengo Oka has been involved in automotive security since 2006. In the past, he worked for Volvo Car Corporation in Sweden on automotive security for connected cars, and for the Bosch group where he co-launched the automotive security practice (ESCRYPT) in Japan. As a Principal Automotive Security Strategist at Synopsys, he focuses on security solutions for the automotive software development lifecycle and supply chain.
Published in Telematics Wire


